Based on the Microsoft AI Boardroom 2025 information, I can analyze the AI adoption patterns in India’s Banking, Financial Services, and Insurance (BFSI) sector and suggest how similar approaches might apply to Singapore’s financial ecosystem.
AI Adoption & Implementation in India’s BFSI Sector
Key Implementation Strategies
- Hybrid Cloud Infrastructure: SBI is transitioning to a model combining a private cloud (Meghdoot) with a public cloud (Azure) to balance security and scalability.
- Purpose-Built AI Solutions: Organizations are developing specialized tools like:
- Bajaj Finserv’s “Enigma” platform for health insurance claims processing
- SBI’s chatbots for specific functions (deceased account settlements, employee assistance)
- Collaborative Approach: Financial institutions are partnering with technology providers rather than building everything in-house.
- Progressive Integration: AI is moving from support functions to core business operations as confidence grows.
Measurable Gains
- Process Efficiency: 40% reduction in claim handling time (Bajaj Finserv)
- Enhanced Fraud Detection: 5x improvement in identifying fraudulent claims
- Operational Consistency: Automation of complex processes like document classification
- Employee Productivity: 65% projected improvement in handling user queries (SBI)
- ROI: Nearly 5x return for every $1 invested in AI
Application to Singapore’s Financial Sector
Singapore’s sophisticated financial sector has different characteristics from India’s but can benefit from similar approaches with some adaptations:
Opportunities for Singapore
- Regulatory Integration
- Singapore’s strict regulatory environment (MAS guidelines) could benefit from AI solutions that ensure compliance while maintaining efficiency.
- AI systems could be designed to automatically adapt to Singapore’s frequent regulatory updates.
- Wealth Management Transformation
- The shift from “physical to virtual relationship management” mentioned by BCG is particularly relevant for Singapore’s substantial wealth management sector.
- Singapore could leverage AI to expand services to a broader range of clients beyond ultra-high-net-worth individuals.
- Security Enhancements
- Given Singapore’s position as a financial hub, implementing solutions like Microsoft’s Copilot for Security could help address the cybersecurity talent shortage.
- Singapore’s connectivity makes it vulnerable to cyber threats, making AI-powered security particularly valuable.
- Cross-Border Applications
- As a regional financial center, Singapore has unique needs for a multi-currency, multi-jurisdiction solution.s
- AI agents could streamline complex cross-border transactions and compliance processes.
- Small Market Advantages
- Singapore’s smaller scale compared to India could allow for faster, more comprehensive AI implementation.
- Higher digital literacy among Singapore’s population may result in faster adoption of AI-enabled services.
Implementation Considerations for Singapore
- Talent Development
- Singapore would need to focus on developing specialized AI talent for financial services.
- The “great equalizer of talent” effect mentioned by BCG could help address Singapore’s limited workforce.
- Data Privacy Balance
- Implementation would need to carefully navigate Singapore’s Personal Data Protection Act (PDPA) requirements.
- Hybrid cloud models like SBI’s could be adapted to meet Singapore’s data sovereignty requirements.
- Public-Private Collaboration
- Singapore could leverage its efficient government-industry collaboration channels to accelerate AI adoption.
- MAS (Monetary Authority of Singapore) could play a coordinating role similar to how Microsoft is helping in India
- Cultural Adaptation
- Customer-facing AI tools would need to be adapted for Singapore’s multicultural context.
- Empathetic AI responses (like those mentioned for Bajaj Finserv’s emotional healthcare context) would need cultural calibration.
Singapore’s advanced digital infrastructure and supportive innovation policies position it well to implement similar or even more advanced AI solutions than those described in India’s BFSI sector, potentially achieving comparable or greater efficiency gains.
AI in Banking: Themes, Challenges, and Implementation Strategies
Major Themes
1. Transformative Potential

- Unprecedented economic opportunity: Potential to boost annual operating profits by £200bn-£340bn
- Comprehensive digital transformation across banking operations
- Shift from traditional banking models to AI-driven, data-centric approaches
2. Strategic Implementation

- Methodical, Phased Transformation Approach
- Compared to steering an “oil tanker” – requiring careful, calculated changes
- Systematic rebuilding of technological architecture
3. Regulatory Compliance and Governance

- Increasing regulatory scrutiny (e.g., EU AI Act)
- Focus on:
- Robust risk management
- Data governance
- Transparency in AI systems
- Human oversight
Key Challenges
1. Data Management
- Fragmented data across multiple systems
- Lack of a Single Source of Truth (SSOT)
- Difficulty in consolidating and standardizing information

2. Technological Integration
- Replacing legacy systems
- Ensuring seamless AI integration
- Managing complex technological transitions

3. Organizational Culture
- Resistance to change
- Need for comprehensive staff training
- Developing AI literacy across the organization
4. Trust and Security
- Maintaining customer confidence
- Balancing innovation with data protection
- Demonstrating transparent and ethical AI use
Implementation Strategies
1. Phased Transformation Approach

- Incremental system upgrades
- Component-by-component modernization
- Controlled risk management
2. Governance Frameworks
- Establish AI governance boards
- Create comprehensive oversight mechanisms
- Develop transparent
 AI use case evaluation processes
AI use case evaluation processes
3. Data Strategy
- Implement open banking principles
- Develop robust data management protocols
- Ensure data quality and standardization

4. Customer-Centric Implementation
- Focus on enhancing customer experience
- Leverage AI to improve service efficiency
- Maintain transparency and build trust
- Practical AI Applications in Banking


1. Customer Service
- AI-enabled contact centers
- Enhanced customer interaction capabilities
- Improved problem resolution efficiency

2. Operational Optimization
- Automated data cleaning
- Testing framework improvements
- Code generation for platform development

3. Risk Management
- Advanced loan and mortgage approval processes
- Intelligent risk assessment
- Regulatory compliance monitoring

Future Outlook
- Continuous adaptation of AI systems
- Emphasis on resilience and flexibility
- Integration of advanced AI with robust security measures

Conclusion
Successful AI implementation in banking requires a holistic approach that balances technological innovation, regulatory compliance, organizational culture, and customer trust.

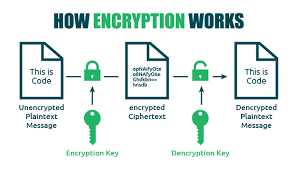
How Encryption Works

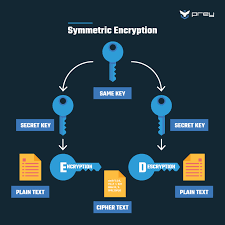
Encryption uses mathematical algorithms to convert plaintext (readable data) into ciphertext (scrambled data). Only those with the decryption key can convert the ciphertext back into usable information. There are two main types:
- Symmetric Encryption: Uses the same key for both encryption and decryption. It’s efficient but requires a secure key exchange.
- Asymmetric Encryption uses a pair of keys—a public key for encryption and a private key for decryption—to allow secure communication without prior key exchange.
Key Encryption Applications for Privacy
Device Encryption
- Full-disk encryption: Protects all data on your computer or smartphone (BitLocker for Windows, FileVault for Mac, and built-in encryption for iOS and Android)
- File-level encryption: Protects individual files and folders

Communication Encryption
- HTTPS: Secures website connections (look for the padlock icon in your browser)
- End-to-end encryption: Used in messaging apps like Signal, WhatsApp, and others to ensure only you and your recipient can read messages
- Email encryption: Options include PGP (Pretty Good Privacy), S/MIME, or encrypted email services
Network Encryption
- VPNs: Create an encrypted tunnel for all your internet traffic
- Wi-Fi encryption: WPA3 is the current most substantial standard for wireless networks
Cloud Storage Encryption
- At-rest encryption: Protects stored data
- Zero-knowledge encryption: The provider has no access to your encryption keys
- Client-side encryption: Data is encrypted before leaving your device

Implementing Encryption in Your Digital Life
- Enable device encryption on all your computers and mobile devices
- Use encrypted messaging apps for sensitive communications
- Verify HTTPS connections when sharing personal or financial information
- Consider encrypted email for sensitive communications
- Choose cloud services with strong encryption policies
- Use a VPN when connecting to public Wi-Fi networks
- Password-protect and encrypt sensitive files and backups
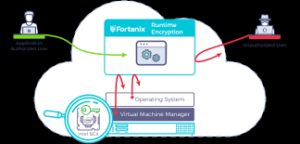
Limitations to Consider
- Encryption can’t protect against malware already on your device
- Weak passwords can undermine even the strongest encryption
- Encryption doesn’t hide metadata (who you’re communicating with, when, how often)
- Some countries have laws limiting encryption use or requiring backdoors

Encryption is a fundamental aspect of digital privacy that works best as part of a comprehensive security strategy. By understanding and implementing appropriate encryption methods, you can significantly enhance your online privacy protection.
.
Identity Theft
Identity theft is a pervasive form of fraud that can have devastating consequences for victims. In this crime, the perpetrator steals an individual’s personal information to assume their identity. This stolen information can often be gathered from discarded documents such as bank statements, utility bills, or even phishing scams.
Once armed with this data, the criminal may choose to open accounts in the victim’s name, a process known as application fraud. They might apply for credit cards, loans, or utility services under pretences, leaving the unsuspecting victim to deal with the aftermath.
The emotional toll of identity theft can be immense. Victims often face financial losses and damage to their credit scores, which can take years. In today’s digital age, account takeovers have become a prevalent threat to unsuspecting victims. Criminals typically employ tactics such as phishing, vishing, or smishing to manipulate individuals into revealing their personal information.

Phishing often involves deceptive emails that appear to come from legitimate sources. These emails may prompt the victim to click on malicious links or provide sensitive details under the guise of verifying their identity.
Vishing, or voice phishing, involves phone calls in which scammers impersonate bank representatives or trusted entities to extract confidential information directly from the victim. Similarly, smishing involves text messages that lure individuals into divulging critical data.
Once armed with this personal information, the criminal can easily convince a bank to change the account holder’s address. This deception allows them full access to the victim’s financial accounts and resources.

Additionally, some criminals are skilled enough to bypass bank interaction altogether. They can use the obtained credentials to log into online accounts directly, executing unauthorised transactions without needing any further verification.
The consequences for victims can be devastating, leading not only to financial loss but also to emotional distress as they recover their stolen identities and secure their accounts. Consequently, individuals must remain vigilant and understand these risks to protect themselves against potential account takeovers for repair. Additionally, they may find themselves tangled in legal disputes as they try to prove their innocence.

Recovering from such a violation requires diligence and time, making it crucial for individuals to safeguard their personal information vigilantly. Implementing measures like shredding sensitive documents and monitoring credit reports can help prevent these types of crimes before they occur.
Maxthon
Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
 This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
