I’m seeing news about a significant data breach affecting customers of DBS Bank and Bank of China in Singapore. Here’s a summary of the key information:
The breach occurred through a ransomware attack on Toppan Next Tech, a printing vendor used by both banks. Approximately 11,200 customers were affected (8,200 from DBS and 3,000 from BOC).
For DBS customers:
- Mainly affected DBS Vickers (brokerage) and Cashline (short-term loan) users
- Compromised data includes names, postal addresses, and details about equities/loans
- The affected documents were from December 2024 to February 2025
For Bank of China customers:
- Compromised data includes names, addresses and some loan account numbers
Important points to note:
- No login credentials, passwords or NRIC details were exposed
- Both banks’ systems remain secure; this was a vendor breach
- No unauthorized transactions have been detected so far
- Both banks have enhanced monitoring on affected accounts and are contacting customers
Toppan reported the attack to authorities on April 6 and has engaged forensic investigators. The Cyber Security Agency of Singapore and the Monetary Authority of Singapore are involved in investigating the incident.
Analysis of the DBS/Bank of China Data Breach
Breach Assessment
This incident represents a significant supply chain attack where threat actors targeted a third-party vendor (Toppan Next Tech) rather than attacking the banks directly. This approach is becoming increasingly common as organizations strengthen their internal security while overlooking vendor vulnerabilities.
Key Observations:
- Attack Vector: Ransomware targeted a printing vendor handling sensitive financial documents, demonstrating how threat actors are targeting the supply chain’s weaker links.
- Data Exposure: Approximately 11,200 customers had personal information compromised, including:
- Names and postal addresses
- Equities holdings information (DBS Vickers)
- Loan account details (Cashline and BOC)
- Limited Scope: The exposure appears contained to specific service lines rather than affecting all bank customers.
- Timing: The compromised documents span a specific period (December 2024 to February 2025), suggesting a defined attack window.
Cybersecurity Implications
For Financial Institutions:
- Third-Party Risk Management Failures: This breach highlights inadequacies in vendor security assessments and ongoing monitoring. Banks must enforce more substantial security requirements for all vendors who handle customer data.
- Data Transmission Security: While DBS mentioned sending encrypted files to Toppan, questions remain about the overall security of the data workflow, including how printed materials are handled and disposed of.
- Regulatory Scrutiny: MAS will likely scrutinize both banks’ vendor management processes and may recommend or mandate stronger controls, potentially affecting the entire Singapore financial sector.
For Affected Customers:
- Identity Theft Risk: The exposed information, while not including passwords or NRIC, provides enough data for social engineering attacks or identity theft attempts.
- Targeted Phishing Campaigns: Customers should be vigilant for sophisticated phishing attempts that leverage the exposed information to appear legitimate.
- Financial Account Monitoring: While no unauthorized transactions have been reported, customers should carefully monitor their accounts for suspicious activities.
Broader Industry Impact:
- Growing Sophistication of Supply Chain Attacks: This breach reflects a trend where attackers strategically target service providers rather than end organizations, exploiting trust relationships.
- Ransomware Evolution: This was a “random ransomware attack” (according to Toppan) that succeeded in capturing valuable financial data, which shows how opportunistic attacks can have major consequences.
- Data Protection Requirements: This incident may accelerate regulatory requirements for data protection in outsourced operations across Singapore’s financial sector.
Strategic Considerations
- Zero Trust Architecture: Financial institutions should implement zero trust frameworks that verify every transaction and access attempt, regardless of source.
- Vendor Assessment Overhaul: Banks need more rigorous and continuous security assessments of their vendors, including requiring SOC 2 compliance or equivalent.
- Data Minimization: The incident raises questions about whether printing vendors need access to as much customer information as they currently receive.
- Incident Response Coordination: The coordinated response between CSA, MAS, and the affected banks demonstrates Singapore’s mature cybersecurity ecosystem, but improvements in vendor incident response protocols are clearly needed.
This breach serves as an important reminder that cybersecurity is only as strong as the weakest link in an organization’s digital supply chain, and that comprehensive security requires vigilance across all data touchpoints.
Preventing Data Leaks in Singapore Banks
Data breaches like the recent incident with DBS and Bank of China highlight vulnerabilities that need addressing. Here’s a comprehensive approach to preventing data leaks in Singapore’s banking sector:
Strengthening Internal Security Controls
- Implement Data Loss Prevention (DLP) systems
- Deploy solutions that monitor, detect, and block sensitive data transfers
- Apply content inspection and contextual security analysis to data in use, in motion, and at rest
- Adopt zero-trust security architecture
- Verify every user and device attempting to access resources
- Apply least-privilege access principles to limit data exposure
- Implement strong authentication mechanisms, including MFA, across all systems
- Enhance data encryption
- Encrypt sensitive data both at rest and in transit
- Implement strong key management practices
- Ensured proper implementation of TLS/SSL protocols for all communications
Improving Third-Party Risk Management
- Rigorous vendor assessment process
- Conduct thorough security audits before onboarding vendors
- Require vendors to demonstrate compliance with standards like ISO 27001, SOC 2, or DORA
- Review vendor security policies, incident response plans, and breach notification procedures
- Contractual safeguards
- Include specific security and privacy requirements in vendor contracts
- Establish clear accountability for data protection
- Define breach notification timelines and responsibilities
- Include right-to-audit clauses and penalties for non-compliance
- Ongoing vendor monitoring
- Implement continuous security monitoring of vendor systems
- Conduct regular security assessments and penetration testing
- Require regular security reports and certifications
Enhancing Data Governance
- Implement data minimization principles
- Only collect and retain necessary customer information
- Limit data sharing with third parties to essential information
- Establish apparent data retention and destruction policies
- Classify and inventory data
- Identify and catalog all sensitive data
- Apply appropriate protection controls based on data classification
- Regularly audit data access and usage patterns
- Establish clear data handling procedures
- Define protocols for data transfers between systems and organizations
- Create strict guidelines for handling sensitive customer information
- Implement secure methods for data destruction
Strengthening Employee Security
- Security awareness training
- Conduct regular security training sessions for all staff
- Include social engineering and phishing awareness
- Establish clear policies for handling sensitive information
- Insider threat mitigation
- Implement behavior analytics to detect unusual access patterns
- Monitor privileged user activities
- Establish separation of duties for sensitive operations
Regulatory Compliance and Beyond
- Follow MAS guidelines rigorously
- Adhere to Technology Risk Management Guidelines
- Implement controls required by the Personal Data Protection Act (PDPA)
- Participate in the MAS Cyber Security Advisory Panel initiatives
- Go beyond compliance
- Treat security as a business enabler rather than just a requirement
- Implement security by design in all systems and processes
- Establish a dedicated cybersecurity team with executive sponsorship
Incident Response Readiness
- Develop comprehensive incident response plans
- Create detailed response procedures for different breach scenarios
- Define clear roles and responsibilities
- Establish communication protocols with regulators and customers
- Regular testing and simulation
- Conduct tabletop exercises and simulated breach scenarios
- Test backup and recovery procedures
- Evaluate response effectiveness and update plans accordingly
- Transparent communication protocols
- Establish clear guidelines for customer notification
- Prepare templates for different breach scenarios
- Train spokespersons on crisis communication
By implementing these measures, Singapore banks can significantly reduce their risk of data breaches and better protect their customers’ sensitive information. The focus should be not just on technology but on creating a comprehensive security culture throughout the organization and its partner ecosystem.
Encryption
HTTPS, or Hypertext Transfer Protocol Secure, represents a fortified version of its predecessor, HTTP (Hypertext Transfer Protocol). While HTTP serves as the framework for transmitting data across the internet in a client-server architecture—where the web browser interacts with the web server—HTTPS takes this a step further by incorporating encryption. This is achieved through an encryption protocol known as Transport Layer Security (TLS), which evolved from the earlier Secure Sockets Layer (SSL). The purpose of this encryption is to make any data exchanged between the browser and server unreadable to unauthorised parties until it reaches its intended recipient, thereby enabling users to transmit sensitive information like passwords and personal details safely over the internet.
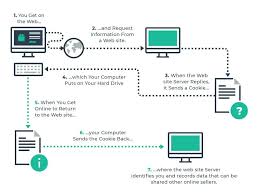
For HTTPS to establish a secure connection, it first needs to build trust between the browser and server. This necessity for trust is underscored by the implementation of HTTP Strict Transport Security (HSTS), which enforces that websites can only be accessed through secure connections.
When compared, HTTPS and HTTP serve similar functions; however, HTTPS distinguishes itself by incorporating an additional layer of security through SSL/TLS encryption. To transition from HTTP to HTTPS, a website must obtain an SSL certificate—often referred to as a security or digital certificate. This small file plays a crucial role in safeguarding sensitive data during transmission by rendering it unreadable while in transit.
The SSL certificate contains a public key that facilitates secure communication from users’ browsers when sending confidential information. Meanwhile, only the domain owner possesses a private key capable of decrypting this information upon arrival at their server. This combination of public and private keys establishes a secure channel for data exchange.
Website owners must acquire an SSL certificate from an accredited Certificate Authority (CA) to enable HTTPS on their domain. When users attempt to connect via HTTPS, their web browsers verify that the provided SSL certificate corresponds with the domain name they intend to visit, ensuring both authenticity and security throughout their online experience.
Why Opt for HTTPS? In today’s digital landscape, HTTPS has emerged as the go-to protocol for online activities, providing the most secure means for users to safeguard their sensitive data. Its importance extends beyond just websites that collect user information; even without direct input from users, malicious actors can gather behavioural and identifying details through unsecured connections. While HTTP might offer some advantages to website owners in terms of functionality and user experience, it pales in comparison to the trust that HTTPS fosters among visitors. With HTTPS, users can verify the legitimacy of a site by checking its SSL Certificate against the domain name.

The encryption provided by SSL/TLS ensures that all interactions between clients and servers remain confidential, making it nearly impossible for attackers to access sensitive data. This level of security is particularly vital for online businesses like e-commerce platforms, where potential customers need reassurance that their payment information is safe from prying eyes. Failing to implement HTTPS not only jeopardises customer privacy but also tarnishes a brand’s reputation; unsecured connections leave customer data vulnerable to breaches that could discourage future business.

As HTTPS has become recognised as the gold standard in web protocols, browsers have responded accordingly. For instance, Google Chrome now actively warns users about HTTP sites, while Mozilla Firefox has introduced an HTTPS-only mode. Additionally, Google’s search algorithm favours HTTPS pages over their HTTP counterparts, meaning site owners stand to gain better visibility and SEO rankings by making the switch. The introduction of HTTP/2 in 2015 further emphasised this shift by enhancing browsing speed and overall user experience with new features—most browsers now restrict HTTP/2 usage exclusively to secure sites utilising HTTPS. Consequently, those still operating on HTTP must adapt if they wish to benefit from these advancements.
How can I enhance the security of my website? If your site collects sensitive user information, implementing HTTPS is crucial. Organisations that prioritise security recognise its significance; hence, you must validate your website before integrating it with third-party services. Take PayPal, for instance—online payment processors typically require a security certificate to process transactions through their platforms. By securing your site, you also build trust with your visitors, reassuring them that their personal information will be kept confidential.
To activate HTTPS on your website, you’ll need to acquire a security certificate from a Certificate Authority (CA). There are six types of certificates available for purchase, each catering to different validation needs and domain structures:
1. Domain Validated (DV) Certificate: Confirms that you control the domain before issuing the certificate.
2. Organization Validated (OV) Certificate: This certifies the site’s ownership and additional details, such as the domain name and its location.
3. Extended Validation (EV) Certificate: This certificate thoroughly verifies the organisation’s ownership, legal status, and geographical location.
4. Single-name Certificate: Secures one specific subdomain hostname.
5. Wildcard Certificate: Covers an unlimited number of subdomains under a single domain.
6. Multi-Domain Certificates: Can protect up to 100 domains, including subdomains and public IP addresses.
After selecting and purchasing your desired certificate from a CA, you’ll need to install it on your server to enable HTTPS functionality—thus ensuring a secure connection.
Is HTTPS Truly Foolproof?
In today’s digital landscape, HTTPS plays a crucial role in safeguarding online interactions through robust encryption and authentication measures. This technology employs a combination of public and private keys to ensure that data exchanged between users’ browsers and servers remains secure. Additionally, HTTPS mandates the use of digital certificates, which serve as proof that a website’s domain name aligns with its legitimate owners.
For businesses handling extensive customer information, obtaining more advanced certifications is often a way to enhance their trustworthiness and reliability in the eyes of consumers. Yet, despite these protective layers, web users need to remain vigilant while navigating the internet. Cybercriminals can create deceptive redirects leading to harmful sites or impersonate well-known domains, tricking unsuspecting individuals into divulging sensitive information.
To protect themselves online, users should always verify that URLs correspond accurately with their intended destinations. They should also be cautious about where personal details like passwords are entered; if a payment page raises any red flags or seems dubious, it’s wise to refrain from proceeding with the transaction.
A reliable way for users to ascertain whether a website is legitimate is to check for an up-to-date certificate issued by a trusted authority. This certificate should clearly display the correct domain name associated with that site. In this ever-evolving digital world, staying alert is critical to ensuring safe browsing experiences.
The Rising Threat of Ransomware
In the ever-evolving landscape of cyber threats, few instil a more profound sense of dread than ransomware. This malicious software casts a long shadow over both corporations and governmental bodies alike, sending shivers down their spines.
Imagine this scenario: A nefarious actor infiltrates your computer or mobile device with harmful software, rendering it inoperable until you comply with their ransom demands. While you’re left in limbo, grappling with the chaos, critical personal and business data hangs in the balance—at risk of destruction or theft. The potential for financial ruin looms large.

Regrettably, many individuals and organisations find themselves reacting to these attacks rather than taking proactive measures to prevent them. “Stay informed about the latest scams and tactics to protect yourself from falling prey,” advises Jeff Taylor, who oversees commercial fraud forensics at Regions Bank. He emphasises that nearly all incidents of ransomware commence with a phishing email or a click on a malicious link, which grants the attackers access to your system. “Take a moment to scrutinise the sender’s email address. Be cautious of unsolicited links or attachments; they could lead you down a dangerous path.”
Yet, amidst this grim reality, there is a glimmer of hope. The Departments of Homeland Security and Justice have teamed up to create a resourceful platform (StopRansomware.gov) designed to assist individuals and organisations in combating these threats effectively.
Furthermore, the American Bankers Association has developed a comprehensive Ransomware Toolkit, which encompasses a structured MAP (Mitigate, Assess, and Prepare) strategy for anyone who suspects they might be under attack from ransomware. With these resources at hand, there’s a pathway to not only defend against such threats but also to navigate the complexities of the digital world with greater confidence.
In the face of a ransomware attack, swift action is paramount to reduce the potential damage. Imagine a bustling office, the hum of computers filling the air, when suddenly, the screens flash with an ominous message demanding payment for the return of critical files. The first step in this chaotic scenario is to identify which devices have fallen victim to this digital menace. Like a detective surveying a crime scene, IT professionals must meticulously isolate the compromised systems. If circumstances allow, the entire network should be taken offline, like closing the doors to prevent any unwelcome intruders from further infiltrating.
As the team gathers information about the infected devices, one crucial rule becomes abundantly clear: do not delete or attempt to repair any corrupted files. In the frantic efforts to restore order, it’s easy to forget that these damaged files hold vital clues to understanding how the breach occurred and what steps need to be taken next. Tampering with this evidence could jeopardise both the investigation and the recovery process, akin to erasing fingerprints at a crime scene.

Meanwhile, amidst the tension, another significant decision looms: Should the affected devices be powered down? While shutting them off might seem like a logical step to contain the infection, it carries its risks. Essential artefacts and evidence could vanish into thin air, leaving behind only questions and uncertainty. Therefore, it falls upon the shoulders of senior leadership to weigh the gravity of virus propagation against the need for evidence preservation. If isolation from the network proves impossible, then powering down those devices may become a necessary evil in the battle against ransomware’s relentless advance.
In this high-stakes environment, every choice matters. The path to recovery begins with careful consideration and decisive action, ensuring that the damage can be mitigated while preserving vital evidence for future prevention.
Assessing the Situation
When faced with the aftermath of a cyberattack, it is crucial first to evaluate the damage inflicted upon your systems. The initial step involves identifying which systems are essential for recovery and prioritising them accordingly. As you embark on this journey of restoration, ensure that you create an image of the affected systems and devices. It’s also vital to gather any pertinent logs or signs of compromise—such as unusual commands—and safeguard this information for further investigation.
Next, take stock of your backup data. Verify that these backups are not linked to the compromised system to avoid the risk of re-infection. To enhance your chances of a successful recovery, consider restoring from the oldest available backup version, ideally one that dates back more than 100 days.
Preparing for Action
As you navigate this tumultuous situation, it’s essential to involve law enforcement in tandem with your legal team. Reach out to agencies like the FBI and the Secret Service, as they can offer valuable intelligence that might help decrypt your systems. They can also guide you through the maze of regulatory reporting requirements that follow such breaches.
In parallel, discuss with senior leadership and your legal advisors whether to pay the ransom cybercriminals demanded. This decision should not be taken lightly, as it involves multiple stakeholders and significant implications.
Another consideration is whether to engage an external forensic firm. Their expertise could prove invaluable in facilitating recovery efforts, assessing the potential consequences of making a payment, and implementing further protective measures.
Don’t forget about your customers; they deserve transparency in light of a data breach. Inform both federal and state authorities regarding the incident and identify those customers whose data may have been compromised. It’s essential to file a Suspicious Activity Report with FinCEN and adhere to your state’s specific data breach notification laws.
Reflecting on these challenges, Taylor remarked, “Regrettably, any business—no matter its size—can fall victim to ransomware attacks. Crafting a response plan is an essential part of the recovery process. Knowing who to contact, how to reach them, and understanding each participant’s role will pave a clearer path toward recovery during what is undoubtedly a highly stressful period.”
Ransomware continues to thrive as a lucrative enterprise for criminals, raking in hundreds of millions from those caught unprepared. Once again, the ABA steps up with critical insights aimed at recognising and thwarting ransomware threats, reminding us all of the importance of vigilance in safeguarding our digital landscapes.
In today’s fast-paced world, countless individuals appreciate the remarkable convenience offered by online banking. With just a few taps on a screen or clicks of a mouse, users can effortlessly access their financial accounts and manage transactions. A recent survey by Chase in 2023 uncovered that a staggering 87 percent of Americans engage with their banking apps at least once a month. Yet, with this increasing reliance on digital banking comes an unsettling rise in cybersecurity threats.

The Federal Deposit Insurance Corporation (FDIC) has taken steps to alert consumers about the prevalence of fraudulent banking websites and deceptive apps designed to pilfer personal information and funds. Awareness of these risks is vital; thus, it’s imperative to adopt measures that safeguard your banking details.
So, how can you ensure the security of your personal financial information? Let’s delve into that question together. First and foremost, it’s essential to understand that while sharing your card number might be commonplace—many retailers, professionals, and online sellers have access to this information—it’s crucial to keep everything else closely guarded. The notion of having your card number out in the open isn’t inherently alarming, but safeguarding the rest of your banking details is paramount. Below are expert recommendations to help you fortify your defenses against potential threats.
Employ Distinct Passwords
You’re likely already aware of the importance of a strong password. However, relying solely on one robust password may not be enough to shield your bank account from the prying eyes of hackers. According to cybersecurity expert Weisman, utilizing the same password across various platforms puts all your accounts at risk. If a hacker manages to uncover one password, they could easily infiltrate your other accounts, including those holding sensitive financial data.
Choose Lengthier Passwords
Consider this: a password consisting of 16 characters boasts exponentially more potential combinations than an eight-character password. This fundamental difference makes it nearly impossible for cybercriminals to successfully employ guessing techniques against longer passwords. As you navigate the complexities of online banking, remember that taking these simple yet effective precautions can significantly enhance the security of your personal banking information.
By embracing these practices, you can enjoy the ease of online banking without constantly looking over your shoulder for lurking threats. In a world where convenience meets risk, being proactive about your security can mean the difference between peace of mind and potential peril.
Safeguarding Your Finances: A Modern Tale
In today’s interconnected world, managing finances can be a perilous endeavor, especially in bustling public spaces where the threat of cyberattacks looms large. Imagine yourself at a café, laptop open, coffee steaming beside you, as you log into your bank account to settle bills or transfer funds. It may seem harmless, but this seemingly innocent act could expose you to significant risks. The reality is that any financial transaction conducted without adequate protection is like sailing a ship through stormy seas without a life raft.
To navigate these treacherous waters, consider the power of a Virtual Private Network (VPN). Think of it as a shield that guards your sensitive information while you’re online. For Mac users, installing a VPN not only secures your data but also acts as a fortress against potential cyber threats. Imagine a vigilant guardian, always on the lookout for anyone trying to snoop on your activities, tamper with your connection, or manipulate your cookies. With VeePN, this guardian stands firm, ensuring that intruders are kept at bay. Plus, with a complimentary trial period available, you can dip your toes into the world of enhanced security without any commitment.
As you venture deeper into the realm of digital banking, consider turning to mobile banking applications. These innovative tools offer an additional layer of security that often surpasses traditional PC access. Picture this: when you log into your banking app, it’s not just your username and password at play; your phone number plays a crucial role too, creating an added barrier against unwanted access. In moments when swift communication is vital, your bank can reach you instantly via text or email, confirming transactions and keeping you informed. Most individuals keep their phones close at hand—almost like an extension of themselves—making it the perfect device for managing finances securely. However, remember to download apps directly from your bank’s official website rather than third-party stores, and always use them on devices you trust.

In this narrative of digital security, multifactor authentication emerges as a formidable ally. This approach demands that you confirm your identity through at least two distinct methods. Envision this: you enter your password (something you know), then receive a text code on your cellphone (something you have), and perhaps even authenticate through a fingerprint scan (something you are). This trifecta of security ensures that even if one line of defense falters, others remain robust. And as you input sensitive information, using tools like VPN Edge or a similar browser extension fortifies your defenses further—ensuring that no sneaky hacker can intercept your credentials.
Lastly, let’s delve into the realm of password management. With so many passwords to juggle—especially for your banking accounts—it can feel overwhelming. Imagine having a trusty companion by your side: a password manager. This tool not only keeps all your passwords safe and sound but also generates strong ones for you, freeing your mind from the burden of remembering every single detail.
Alternatively, if technology isn’t your cup of tea, jotting down your passwords might be an option. Just ensure they are stored securely away from prying eyes.
Embrace the Power of a Password Manager
In an age where digital security is paramount, navigating the labyrinth of passwords can feel daunting, particularly when it comes to protecting sensitive information like bank account details. Imagine having a trusty companion by your side—this is precisely what a password manager offers. These ingenious tools not only allow you to securely store your various passwords, freeing your mind from the burden of memorization, but they also can create strong, unique passwords for each of your accounts. With a password manager, you can rest easy, knowing that your online security is in capable hands.
Now, if technology isn’t quite your forte or you prefer a more traditional approach, there’s always the option of jotting down your passwords on paper. Should you decide to go this route to safeguard your financial information from potential fraudsters, it’s crucial to keep that written record locked away in a secure location. After all, the safety of your credentials relies heavily on keeping them out of reach from prying eyes.
Stay Alert with Email Notifications
Rewind a few years, and many customers found themselves blissfully unaware of fraudulent activities until their monthly bank statements arrived in the mail. This delay often resulted in weeks of unchecked, unauthorized transactions, allowing fraudsters to wreak havoc. However, thanks to modern alert systems, things have taken a turn for the better. Now, individuals receive immediate notifications about suspicious activity, empowering them to act swiftly in collaboration with their banks to address any discrepancies before they spiral out of control.
Be Wary of Deceptive Communications
As we traverse this digital landscape, it’s vital to remain vigilant against potential threats. Expert advice suggests steering clear of unfamiliar messages and the links they may contain. It’s essential to remember that legitimate banks and credit unions will never reach out requesting sensitive information that they already possess, such as your account number. If you ever find yourself uncertain about a communication, take a moment to contact your bank or credit union directly before divulging any personal information online or through text. This simple step can save you from potential heartache.

The Bigger Picture
Reflecting on the broader implications of these actions reveals a stark reality: According to reports from the Federal Trade Commission, consumers collectively lost nearly $9 billion to fraud in 2022—a staggering 30 percent increase from the previous year. By staying informed about the ever-evolving landscape of cybercrime and equipping yourself with knowledge on how to protect your personal information, you can take proactive steps to ensure that you don’t become just another statistic in this alarming trend. The journey toward cybersecurity is ongoing, but with awareness and the right tools at your disposal, you can navigate it confidently and safely.

How HTTPS Ensures Cybersecurity in the Maxthon Browser
1. Understand HTTPS Basics: HTTPS, or HyperText Transfer Protocol Secure, is an extension of HTTP that uses encryption to secure data exchanged between the browser and web servers.
2. Encryption Mechanism: When you visit a website that uses HTTPS in the Maxthon browser, your connection is encrypted using SSL/TLS protocols. This means that any data transmitted—such as passwords or credit card information—is scrambled and unreadable to potential eavesdroppers.
3. Data Integrity: HTTPS ensures that the data sent and received has not been altered during transmission. If any tampering occurs, the connection will be terminated, protecting you from malicious local attacks.
4. Authentication Verification: Maxthon’s browser verifies the authenticity of websites through digital certificates issued by trusted Certificate Authorities (CAs). This helps to confirm that you are communicating with a legitimate website and not an imposter.

5. Visual Indicators: Look for visual cues in the address bar when using Maxthon. A padlock icon signifies a secure connection, and it serves as an easy reference point to gauge whether your browsing session is protected.
6. Protection Against Phishing Attacks: HTTPS can help mitigate phishing threats, in which attackers attempt to trick users into providing sensitive information on fraudulent sites. By ensuring that you’re connected to verified websites, HTTPS can help mitigate phishing attacks.
7. Automatic Redirects: The Maxthon browser often supports automatic redirection from HTTP to HTTPS sites whenever available, further enhancing security without requiring additional user intervention.
8. Regular Updates and Compliance: To ensure continued protection, keep your Maxthon browser up-to-date; updates often include patches for vulnerabilities in encryption protocols or other security measures.
9. Educate Yourself on Safe Browsing Practices: Familiarize yourself with additional cybersecurity practices—such as recognizing secure websites and understanding online threats—to maximize your safety while using Maxthon with HTTPS enabled.
By following these principles and leveraging HTTPS features within Maxthon, you enhance your overall cybersecurity while navigating the web.
