I’ve read Jonathan Eyal’s article “Trump’s silencing of US spooks,” which discusses concerns about President Trump’s approach to the US intelligence community since returning to the White House in January 2025.
The key points from the article include:
- President Trump recently fired General Timothy Haugh, director of the National Security Agency (NSA), reportedly based on accusations of disloyalty from Laura Loomer, a right-wing influencer and Trump ally.
- The article argues that Trump has appointed loyalists to key intelligence positions, including Kash Patel as FBI director and Tulsi Gabbard as Director of National Intelligence.
- It suggests Trump has a long-standing distrust of intelligence agencies dating back to his first term, when allegations about Russian interference in the 2016 election created tension between him and the intelligence community.
- The author expresses concern that political interference could lead to self-censorship within intelligence agencies, where information that contradicts the president’s views might be downplayed or ignored.
- The article warns this approach could damage relationships with “Five Eyes” intelligence partners (Australia, Britain, Canada, and New Zealand) and ultimately reduce the effectiveness of US intelligence.
The article presents a perspective that President Trump is subordinating intelligence functions to personal loyalty rather than allowing agencies to “speak truth to power,” which the author argues could have negative consequences for US security and international relationships.
Based on the article provided, there’s no clear evidence that President Trump is specifically targeting or removing “leftists” from intelligence positions. The article doesn’t frame the intelligence community changes in terms of ideological purges (left vs. right), but instead focuses on concerns about loyalty to Trump personally.
The article mentions:
- General Timothy Haugh was fired as NSA director, but there’s no indication that this was due to leftist ideology—rather, the article attributes it to Laura Loomer’s accusation of “disloyalty.”
- Kash Patel (FBI Director) has reportedly targeted what he calls “members of the deep state,” with one Russia expert being removed, but this appears to be based on Patel’s perception of their opposition to Trump rather than leftist political leanings specifically.
- The article suggests the concern is about intelligence professionals being removed or silenced for providing information that contradicts Trump’s views, not necessarily for holding leftist political positions.
The article’s central concern is that intelligence agencies may be required to provide information that aligns with the president’s existing beliefs rather than objective analysis, regardless of political ideology. It focuses on loyalty to Trump personally rather than ideological screening of intelligence officials.
Without additional information beyond what’s in this article, it would be an overstatement to characterise the changes as specifically targeting leftists in intelligence agencies.
Based on the article, there is indeed a significant concern being raised that President Trump is prioritising personal loyalty over professional competence or objectivity in intelligence leadership positions.
The article highlights explicitly:
- The author argues that Trump demands “total loyalty from the IC, a loyalty not only to the institution of the American President and commander-in-chief, but also a personal loyalty to him and all his ideas, regardless of how bizarre these may be.”
- General Timothy Haugh’s firing appears to exemplify this concern—he was dismissed not for any professional failing but because Trump ally Laura Loomer labelled him “disloyal.”
- Kash Patel’s appointment as FBI director is presented as concerning because he published an “enemies list” of supposed “deep state” members and has reportedly begun removing individuals he targeted in his book.
- Tulsi Gabbard’s control over the President’s Daily Brief suggests information is being filtered to align with what she “considers reliable,” potentially limiting what intelligence reaches the president.
The article frames this as a departure from the norm where intelligence professionals are selected primarily for their expertise and ability to provide objective analysis. The author argues that while political alignment has always played some role in intelligence leadership, the current situation appears more extreme, with loyalty to Trump personally becoming the paramount qualification.
The key concern expressed is that this approach could lead to self-censorship within intelligence agencies and ultimately degrade the quality and objectivity of intelligence provided to decision-makers.
Trump’s Relationship with the CIA and FBI
Based on the article provided, I can offer an analysis of President Trump’s relationship with U.S. intelligence agencies, specifically the CIA and FBI. However, the information is limited to what’s presented in this single source.
Historical Context
According to the article, Trump’s relationship with intelligence agencies has been contentious from the beginning of his political career:
- Unlike most presidents who enter office with some prior experience working with intelligence services, Trump had no such background.
- His initial relationship with intelligence agencies was colored by investigations into Russian interference in the 2016 election, which he perceived as questioning the legitimacy of his victory.
- Though he attempted to reset relations on January 21, 2017 (the day after his first inauguration) with a visit to CIA headquarters, the article describes this as “a classic Trumpian-style disaster” that deteriorated into “a rambling rant.”
- During his first term, he publicly criticised intelligence chiefs when their assessments contradicted his views, particularly regarding Iran’s nuclear program.
Current Approach (2025)
The article describes Trump’s return to power in January 2025 as being characterised by:
- A desire for “total loyalty” from intelligence agencies
- Appointments of perceived loyalists to key positions
- What appears to be retribution against a perceived “Deep State”
Key Appointments Affecting the FBI & the Intelligence Community
- Kash Patel as FBI Director: Described as having published an “enemies list” of 60 people he calls “members of the deep state” and promising to turn the FBI headquarters into a “museum to the deep state.” The article mentions that one FBI agent and Russia expert identified by Patel has already been removed.
- Tulsi Gabbard, as Director of National Intelligence, now exercises direct control over the President’s Daily Brief, potentially filtering what intelligence reaches the president according to her own criteria.
Core Issues
The article identifies several concerning dynamics in Trump’s approach to intelligence agencies:
- Personalisation of loyalty: Demanding loyalty not just to the office of the presidency but to Trump personally and his worldview
- Politicisation of analysis: Intelligence assessments potentially being shaped to match Trump’s preferences rather than objective analysis (for example, regarding Russia’s role in starting the Ukraine war)
- Morale and retention issues: The article suggests that “abrupt dismissals” could “demoralise capable agents, increase the number of capable officials who leave the service”
- Self-censorship: Intelligence professionals potentially avoiding collecting or analysing information that might contradict the president’s views
The Distinction Between Politics and Intelligence
The article acknowledges that politics has always influenced intelligence to some degree, noting that political considerations play a role in appointments even in countries like Australia and Britain that pride themselves on professional intelligence services. It also recognises that politicians have the right and sometimes the duty to make decisions that go against intelligence recommendations.
However, it draws a line at compelling intelligence agencies “to ignore the collection or the interpretation and analysis of information just because they know that the findings contradict the established opinions of their political masters.”
The article’s central concern isn’t that Trump is making political appointments (which all presidents do), but that he appears to be demanding that intelligence agencies conform their analysis to his pre-existing views rather than providing objective information that might sometimes challenge those views.
The article discusses concerns about President Trump’s approach to the US intelligence community, focusing on issues like:
- Demanding personal loyalty from intelligence officials
- Appointing loyalists to key positions
- Dismissing professionals based on perceived disloyalty
- Potentially creating an environment where intelligence is filtered to match the president’s existing views
While the author expresses concern about these trends and their potential impact on intelligence quality and relationships with allies, the article does not characterize these actions as resembling Nazi tactics or draw any such historical comparison.
Countermeasures in the Singapore Context
1. Legal and Regulatory Framework
- Cybersecurity Act (2018): Establishes a framework for the protection of Critical Information Infrastructure
- Computer Misuse Act: Criminalizes unauthorized access and other cyber offenses
- Personal Data Protection Act (PDPA): Governs collection, use, and disclosure of personal data
- Cybersecurity Labeling Scheme (CLS): Rates IoT devices on security levels

2. National Initiatives
- Singapore Cyber Security Agency (CSA) leadership in national cybersecurity strategy
- SG Cyber Safe Programme to raise businesses’ cybersecurity awareness
- Singapore’s National Cybercrime Action Plan
- Digital Defense pillar of Total Defense framework

3. Technical Measures
- Advanced Threat Intelligence solutions tailored to Singapore’s threat landscape
- Multi-factor authentication is mandatory for sensitive systems (like SingPass)
- Virtual Private Networks for secure remote connections
- Cybersecurity health checks for businesses
- Secure web gateways to filter malicious content

4. Education and Awareness
- Cybersecurity awareness campaigns (like CSA’s “Better Cyber Safe Than Sorry”)
- Scam Alert website and app providing real-time information on scams
- Digital Defense Badge program for students
- SME Go Digital program with cybersecurity components
- Industry-specific awareness training for high-risk sectors

5. Public-Private Partnerships
- Collaboration between government agencies, businesses, and academia
- Information sharing platforms like the Singapore Computer Emergency Response Team (Singcert)
- Joint exercises to test cybersecurity preparedness
- Industry-specific security guidelines

Singapore-Specific Recommendations
- Implement Singapore’s SMS Sender ID Registry to reduce SMS phishing attacks.
- Adopt National Digital Identity solutions like SingPass Face Verification
- Participate in sector-specific threat sharing groups coordinated by CSA
- Implement the Cybersecurity Toolkit for SMEs developed by IMDA and CSA
- Regular employee training on Singapore-specific scam tactics
- Monitor government alerts from SingCERT and ScamShield
- Deploy AI-based threat detection systems calibrated to local threat patterns
- Conduct regular security assessments aligned with MAS/IMDA guidelines
- Engage with Singapore Security Operations Centres (SOCs) for continuous monitoring
- Develop incident response plans compliant with local regulatory requirements

- Keep devices updated: Regularly update your computer and mobile devices to patch security vulnerabilities.
- Use security software: Install antivirus and anti-malware protection on your computers and schedule regular scans.
- Practice good password habits: Create strong, unique passwords for each account, enable multi-factor authentication, and avoid sharing passwords.
- Secure your home network: Set strong Wi-Fi passwords, use proper encryption (at least WPA2), update router software, and consider hiding your network.
- Defend against phishing/vishing: Be vigilant about suspicious emails or calls requesting personal information, and verify legitimacy through official channels.
- Back up your data: To recover from potential compromises, regularly copy files to external storage or secure cloud services.
- Educate family members: Discuss internet security with children and older relatives who may be vulnerable to different types of cyber threats.
- Prevent identity theft: Shred sensitive documents, avoid suspicious links, and regularly review your credit report.
- Know what to do if victimised: Consider enabling fraud alerts or credit freezes if your information is compromised.
- Control your information: Be cautious about sharing sensitive information online and regularly review privacy settings.
According to the article, the global financial impact of cyber fraud is rising dramatically, with victims losing $37.4 billion to cybercriminals in the past five years. Phishing scams are the most common, while investment scams are the costliest (over $4.5 billion lost in 2023).

The article also mentions that scammers are increasingly using AI tools like deepfakes and large language models to create more sophisticated fraud attempts.

Crime Prevention Methods
Crime prevention encompasses a variety of strategies designed to reduce criminal activity by addressing its root causes and opportunities. Here are the main approaches to crime prevention:
Situational Crime Prevention
These methods focus on reducing opportunities for crime by making criminal acts more difficult and risky:
- Target hardening: Using physical barriers like locks, alarms, and security systems to protect property
- Access control: Limiting entry to specific areas through key cards, security gates, or doormen
- Natural surveillance: Designing spaces to increase visibility (better lighting, removing visual obstructions)
- CCTV and surveillance: Installing cameras and monitoring systems to deter criminals and collect evidence
- Environmental design: Using CPTED (Crime Prevention Through Environmental Design) principles to create safer spaces

Social Crime Prevention
These strategies address the underlying social factors that contribute to crime:
- Education and awareness programs: Teaching people about risks and prevention strategies
- Community engagement: Neighbourhood watch programs, community policing initiatives
- Youth intervention programs: After-school activities, mentoring, and education to provide positive alternatives
- Economic opportunity development: Job training, employment programs, and economic revitalisation
- Family support services: Counselling, parenting classes, and support for at-risk families

Law Enforcement Strategies
Proactive approaches by police and criminal justice systems:
- Hot spot policing: Concentrating resources in high-crime areas
- Problem-oriented policing: Identifying and addressing specific crime problems
- Intelligence-led policing: Using data analysis to predict and prevent crime
- Swift and inevitable consequences: Ensuring quick and consistent responses to criminal behaviour
- Focused deterrence: Targeting specific criminal behaviours with enhanced enforcement

Technological Prevention
Using technology to prevent various types of crime:
- Cybersecurity measures: Firewalls, anti-virus software, encryption, and multi-factor authentication
- Biometric security: Fingerprint scanners, facial recognition, and other identity verification methods
- Smart home security: Internet-connected security systems that can be monitored remotely

- Location tracking: GPS monitoring for high-risk offenders
- Data analytics: Using big data to identify patterns and predict potential criminal activity
Individual Prevention Measures
Steps that individuals can take to reduce their risk:
- Personal awareness: Being alert to surroundings and potential dangers
- Target removal: Not displaying valuables, securing personal information
- Routine adjustments: Varying routes and schedules to avoid predictability
- Self-defence training: Learning physical defence techniques and situational awareness
- Building social connections: Developing networks of neighbours who watch out for each other
Each approach has strengths and limitations, and the most effective crime prevention strategies employ multiple methods in coordination.

Crime Prevention Methods in Singapore
Singapore is known for its low crime rates and effective crime prevention strategies. Here’s how the various crime prevention methods are applied in the Singapore context:
Situational Crime Prevention in Singapore
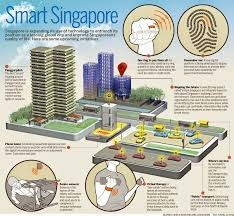
- Extensive CCTV network: Singapore has one of the world’s most comprehensive public surveillance systems with over 90,000 police cameras installed across public housing estates, public areas, and transportation networks.
- Smart Nation initiatives: The government’s Smart Nation program includes sensors and surveillance technologies that enhance public safety.
- Housing design: HDB (Housing & Development Board) flats are designed with security features and community spaces that promote natural surveillance.
- Police cameras: The PolCam initiative places police cameras in public housing blocks and common areas to deter crime and aid investigations.
- Secured By Design: Commercial buildings and public facilities implement crime prevention through environmental design principles.
Social Crime Prevention in Singapore

- Community Policing: The Singapore Police Force’s Community Policing System divides neighbourhoods into smaller sectors with dedicated Neighbourhood Police Centres.
- Citizens on Patrol: Volunteer residents patrol their neighbourhoods alongside police officers.
- Yellow Ribbon Project: Rehabilitation and reintegration programs for ex-offenders to reduce recidivism.
- Racial Harmony policies: Programs that promote social cohesion and reduce tensions between different ethnic groups.
- Education system: Schools incorporate character development and values education to promote law-abiding behaviour.

Law Enforcement Strategies in Singapore

- Swift and sure justice: Singapore’s criminal justice system is known for its efficiency and certainty of punishment.
- Deterrent sentencing: Relatively harsh penalties for crimes serve as strong deterrents.
- Low corruption: Strong anti-corruption measures ensure police integrity.
- Data-driven policing: The Police Intelligence Department uses analytics to identify crime patterns and deploy resources effectively.
- Community engagement: Regular community outreach by Neighbourhood Police Centres helps build trust and gather intelligence.
Technological Prevention in Singapore
- National Digital Identity System: Singpass provides secure digital identification for government and financial services.
- Cybersecurity infrastructure: The Cyber Security Agency of Singapore coordinates national efforts to protect critical infrastructure.
- Police technology: Advanced tools like the POLCAM 2.0 with analytics capabilities and the i-Witness mobile app for citizens to report incidents.
- Smart lamp posts: As part of Smart Nation initiatives, lamp posts equipped with sensors and cameras enhance public safety.
- Cashless society initiatives: Reducing cash transactions helps prevent certain types of theft and robbery.

Individual Prevention Measures Promoted in Singapore
- SGSecure app: A mobile application that allows citizens to report suspicious activities and receive emergency alerts.
- Public education campaigns: Regular campaigns like “Low Crime Doesn’t Mean No Crime” remind citizens to remain vigilant.
- Crime prevention messaging: Frequent public service announcements about scams and new crime trends.
- Neighbourhood watch groups: Resident committees and neighbourhood watch groups in residential areas.
- Public transport safety: Campaigns educating commuters about safety measures and reporting mechanisms.
Unique Aspects of Singapore’s Approach
- Total Defence: A national ideology that includes social and psychological defense against crime.
- Multi-agency collaboration: Different government agencies work together on crime prevention.
- Strict regulations: Controls on weapons, drugs, and public disorder serve as preventative measures.
- Community involvement: Strong emphasis on citizen participation in crime prevention.
- Integrated approach: Combining strict enforcement with rehabilitation and social support.
Singapore’s success in maintaining low crime rates is attributed to this comprehensive, multi-faceted approach that combines strong enforcement with community engagement and technological innovation.
Secure browsing
When it comes to staying safe online, using a secure and private browser is crucial. Such a browser can help protect your personal information and keep you safe from cyber threats. One option that offers these features is the Maxthon Browser, which is available for free. It comes with built-in Adblock and anti-tracking software to enhance your browsing privacy.

Maxthon Browser is dedicated to providing a secure and private browsing experience for its users. With a strong focus on privacy and security, Maxthon employs strict measures to safeguard user data and online activities from potential threats. The browser utilises advanced encryption protocols to ensure that user information remains protected during internet sessions.
In addition, Maxthon implements features such as ad blockers, anti-tracking tools, and incognito mode to enhance users’ privacy. By blocking unwanted ads and preventing tracking, the browser helps maintain a secure environment for online activities. Furthermore, incognito mode enables users to browse the web without leaving any trace of their history or activity on the device.
Maxthon’s commitment to prioritising the privacy and security of its users is exemplified through regular updates and security enhancements. These updates are designed to address emerging vulnerabilities and ensure that the browser maintains its reputation as a safe and reliable option for those seeking a private browsing experience. Overall, Maxthon Browser offers a comprehensive set of tools and features aimed at delivering a secure and private browsing experience.
Maxthon Browser, a free web browser, offers users a secure and private browsing experience with its built-in Adblock and anti-tracking software. These features help to protect users from intrusive ads and prevent websites from tracking their online activities. The browser’s Adblock functionality blocks annoying pop-ups and banners, allowing for an uninterrupted browsing session. Additionally, the anti-tracking software safeguards user privacy by preventing websites from collecting personal data without consent.
By utilising the Maxthon Browser, users can browse the internet confidently, knowing that their online activities are shielded from prying eyes. The integrated security features alleviate concerns about potential privacy breaches and ensure a safer browsing environment. Furthermore, the browser’s user-friendly interface makes it easy for individuals to customise their privacy settings according to their preferences.
Maxthon Browser not only delivers a seamless browsing experience but also prioritises the privacy and security of its users through its efficient ad-blocking and anti-tracking capabilities. With these protective measures in place, users can enjoy the internet while feeling reassured about their online privacy.
In addition, the desktop version of Maxthon Browser works seamlessly with their VPN, providing an extra layer of security. By using this browser, you can minimise the risk of encountering online threats and enjoy a safer internet experience. With its combination of security features, Maxthon Browser aims to provide users with peace of mind while they browse.
Maxthon Browser stands out as a reliable choice for users who prioritise privacy and security. With its robust encryption measures and extensive privacy settings, it offers a secure browsing experience that gives users peace of mind. The browser’s commitment to protecting user data and preventing unauthorised access sets it apart in the competitive web browser market.
