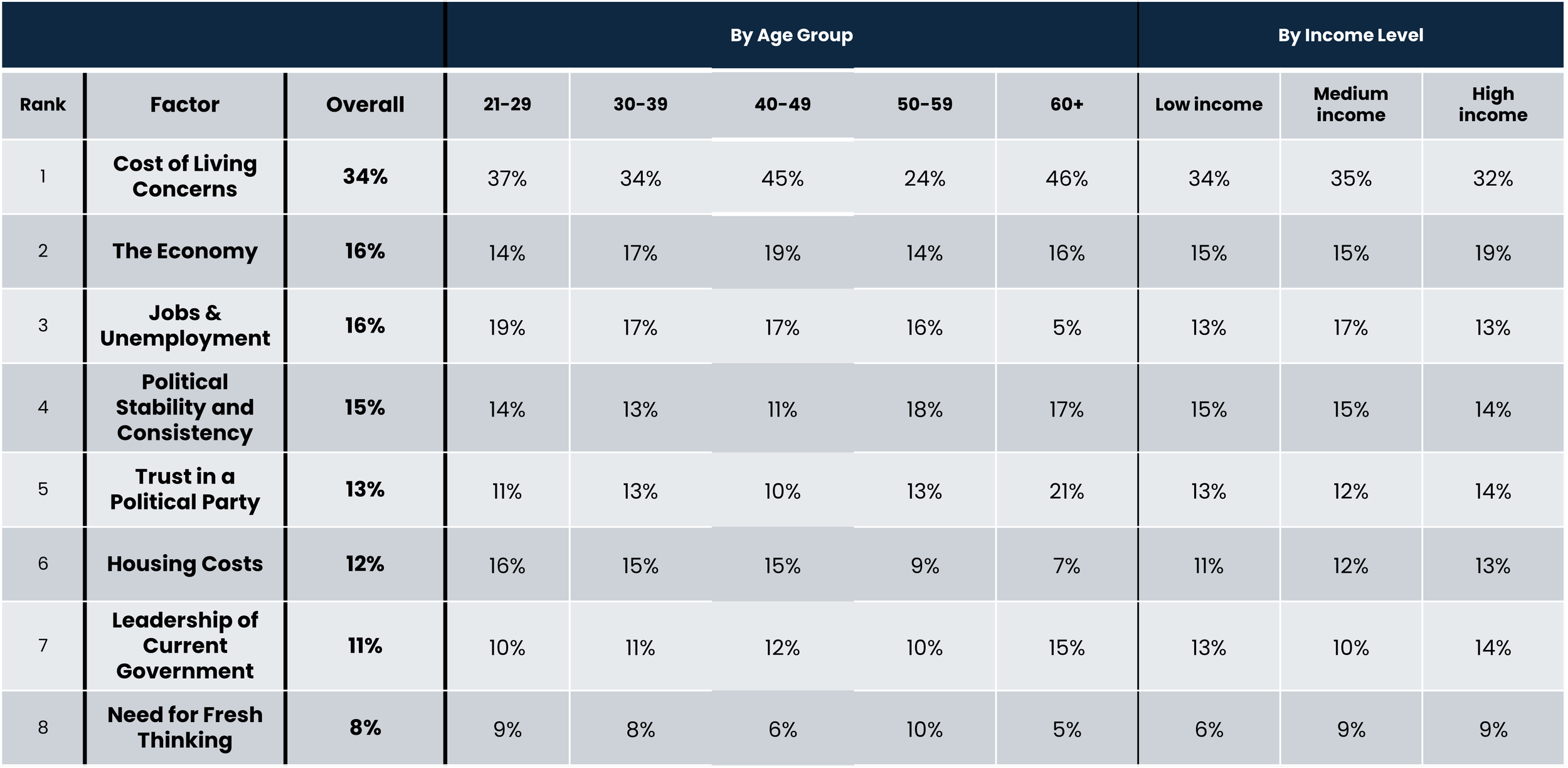
The Cyber Security Agency of Singapore (CSA) has issued important guidelines to protect the electoral process from cyber threats. These recommendations are equally valuable for preventing scams, particularly those targeting high-profile individuals or organisations.
Key Protective Measures Recommended by CSA
- Strong Authentication Controls
- Use complex, unique passwords for all campaign accounts
- Implement multi-factor authentication for email, social media, and internal systems
- Strictly control remote access to digital assets
- System Resilience Planning
- Deploy backup systems and load balancers
- Establish secure secondary communication channels
- Schedule regular software updates and data backups
- Deepfake Detection and Prevention
- Establish protocols for verifying potentially manipulated content
- Train staff to recognise signs of compromise
- Encourage reporting of suspicious incidents
- Management of Digital Assets
- Maintain a complete inventory of all digital assets
- Clear documentation of what data is stored and where
- Implement intrusion detection systems for networks and devices
- Designated Security Leadership
- Appoint experienced personnel to oversee cybersecurity
- Consider third-party security vendor partnerships for additional oversight
Real-World Election Cybersecurity Incidents
The article mentions several concerning examples:
- Polish Prime Minister Donald Tusk reported IT systems attacks ahead of their May elections
- US presidential campaign phone targeting through Verizon’s systems
- Deepfake impersonations of Singapore leaders promoting cryptocurrency scams

How These Measures Apply to Anti-Scam Efforts
These cybersecurity guidelines parallel effective anti-scam strategies. Individuals and organizations can adapt these electoral security practices to prevent falling victim to sophisticated scams:
- Authentication Best Practices
- Use different complex passwords across platforms
- Enable two-factor authentication for financial and social accounts
- Be suspicious of any request to bypass security protocols
- Verification Protocols
- Establish clear channels for verifying unusual requests
- Create communication redundancy (secondary ways to confirm unusual requests)
- Implement verification protocols for financial transactions
- Deepfake Awareness
- Learn to recognize signs of AI-generated or manipulated media
- Verify unexpected communications through alternative channels
- Report suspicious impersonation attempts to authorities
The rising threat of deepfakes in particular represents a significant challenge, as scammers increasingly use AI to create convincing impersonations of trusted individuals, which can be extremely persuasive in donation scams or investment fraud schemes.

The Singapore Police Force and Ministry of Digital Development and Information have highlighted several essential concerns:
- They’re warning against spreading misinformation, online harassment, and content that could incite racial or religious tensions.
- The authorities specifically mentioned the risk of deepfakes, citing a recent incident involving former president Halimah Yacob, who reportedly filed a police report about a fake video showing her making negative comments about the Government.
- The statement outlines several laws under which offenders could be prosecuted:
- Miscellaneous Offences Act
- Protection from Online Falsehoods and Manipulation Act
- Parliamentary Elections Act
- Protection from Harassment Act
- Penal Code
- Maintenance of Religious Harmony Act
- The key dates mentioned are Nomination Day on April 23 and polling on May 3, 2025.
This appears to be part of Singapore’s efforts to maintain order and prevent divisive content during a sensitive political period.

Analysis of Election-Related Online Threats and Prevention Strategies
Fake News During Elections
Elections are particularly vulnerable to misinformation for several reasons:

- High stakes environment: The competitive nature of elections creates incentives for actors to spread misleading content to influence outcomes.
- Speed of information flow: During election periods, there’s pressure to consume and share information quickly, often before proper verification.
- Technological evolution: As seen in Singapore’s warning about deepfakes, advanced AI technologies make fabricated content increasingly convincing and difficult to detect.
- Emotional engagement: Election content often triggers strong emotional responses, making people more likely to share without critical evaluation.
Online Aggressive Behavior During Elections
Political tensions frequently manifest as aggressive online behaviour during elections:
- Polarization: Election periods naturally emphasise differences, which can intensify tribalism and hostile communication.
- Doxxing and harassment: The Singapore authorities specifically warned against publishing personal information to harass political figures or voters.
- Racial and religious tensions: Elections can sometimes be exploited to inflame existing social divisions, as highlighted in Singapore’s warning about content that could “wound racial feelings.”
- Intimidation tactics: Online aggression may attempt to silence sure voters or discourage participation.
Prevention Strategies
Effective prevention requires multi-layered approaches:
- Legal frameworks: Singapore employs multiple laws to address different aspects of online misconduct, creating comprehensive coverage.
- Media literacy initiatives: Teaching citizens to critically evaluate information sources, identify manipulation techniques, and verify claims before sharing.
- Platform responsibility: Social media companies can implement election-specific measures like enhanced fact-checking, clear labelling of synthetic media, and temporary changes to sharing algorithms.
- Official information channels: Establishing authoritative sources for election information helps counter misinformation.
- Cross-sector collaboration: Coordination between government agencies, technology companies, civil society, and media organisations strengthens monitoring and response capabilities.
Anti-Scam Protection
Election periods often see increases in politically themed scams:
- Donation scams: Fraudsters impersonate candidates or parties soliciting donations.
- Registration scams: Fake websites or messages claiming to help with voter registration while stealing personal information.
- Misinformation about voting procedures: False information about voting locations, times, or methods to suppress participation.
Protection strategies include:
- Official verification channels: Directing voters to use only official government websites for election information.
- Digital hygiene practices: Reinforcing basic security measures like checking website URLs, being suspicious of unsolicited messages, and verifying requests through official channels.
- Reporting mechanisms: Establishing clear pathways for citizens to report suspected scams or misinformation.
- Public education campaigns: Proactive alerts about common election-related scams and how to avoid them.
Singapore’s approach demonstrates how countries are increasingly recognising that protecting electoral integrity requires addressing both the technological and social dimensions of online threats.
Mitigating Online Aggressive and Harmful Conduct
Understanding the Problem
Online aggression and harmful conduct manifest in various forms:
- Direct harassment: Targeted threats, insults, and intimidation
- Coordinated attacks: Mobilising groups to target individuals
- Hate speech: Content attacking individuals based on identity
- Disinformation campaigns: Spreading false information to inflame tensions
- Doxxing: Publishing private information without consent

Mitigation Strategies
Technical Solutions
- Content moderation systems
- AI-powered detection of harmful language and threats
- User-reporting mechanisms with rapid response protocols
- Content throttling for potentially inflammatory material
- Temporary conversation “cooling” periods during heightened tensions
- Platform design modifications
- Friction points before posting emotional content (“Are you sure?”)
- Default privacy settings that protect vulnerable users
- Circuit breakers that limit virality of borderline content
- Content labels providing context for controversial topics
- Identity verification options
- Tiered verification systems balancing anonymity and accountability
- Pseudonymous authentication that maintains privacy while reducing bad actors
- Reputation systems rewarding constructive participation
Social and Educational Approaches
- Digital citizenship education
- School curricula on responsible online communication
- Public awareness campaigns about online behaviour impact
- Community workshops on conflict de-escalation techniques
- Community building
- Establishing clear norms and expectations for online spaces
- Training community moderators in de-escalation techniques
- Creating positive incentives for constructive dialogue
- Building platforms for diverse engagement across different viewpoints
- Media literacy programs
- Training on emotional manipulation techniques
- Tools to identify divisive content designed to trigger outrage
- Critical evaluation skills for information sources
Legal and Policy Frameworks
- Balanced regulation
- Clear legal definitions of harmful conduct with proportional consequences
- Protections for legitimate free expression while addressing genuine harm
- International coordination on cross-border enforcement
- Platform accountability
- Transparency requirements on content moderation policies and outcomes
- Due process requirements for content removal
- Requirements for accessible reporting mechanisms
- Specialised response units
- Law enforcement teams trained in digital investigation
- Cross-sector coordination between platforms, civil society, and authorities
- Rapid response protocols for threats of physical harm
Psychological Approaches
- Bystander intervention training
- Teaching witnesses how to safely intervene in online harassment
- Creating cultures where silence is not the default response
- Support systems for targets
- Accessible mental health resources for those experiencing online abuse
- Technical support for securing accounts and personal information
- Peer support networks for sharing coping strategies
- Rehabilitation approaches
- Programs addressing underlying causes of harmful behaviour
- Restorative justice options where appropriate
Implementation Challenges
Effective mitigation must navigate several tensions:
- Free expression vs. harm prevention: Balancing open discourse with protection from genuine harm
- Anonymity vs. accountability: Preserving privacy benefits while reducing consequence-free hostility
- Speed vs. accuracy: Responding quickly while ensuring fairness
- Universal vs. contextual: Developing global standards while respecting cultural differences
- Technology vs. human judgment: Balancing automated systems with human review
The most effective approaches combine multiple strategies tailored to specific contexts, recognising that online aggression has complex social, psychological, and technical dimensions that require coordinated solutions.
The Cyber Security Agency of Singapore (CSA) has issued an advisory warning Singaporeans about potential cyber threats as the May 3 Polling Day approaches. They highlight several specific concerns:
- Fraudsters may create fake social media accounts and political party websites or send phishing emails to solicit fraudulent donations.
- AI is being used to create highly personalised phishing attempts, including convincing emails, messages, and voice clones. Scammers might analyse people’s backgrounds to develop targeted scam tactics aligned with their political views.
- There’s the risk of malware distribution through fake campaign apps and malicious links in emails or SMS messages.
- Deepfakes may be used to falsely show candidates saying or doing things they never did, damaging their reputation.
CSA recommends several protective measures:

- Carefully examine any links in messages and cross-reference with official websites.
- Avoid clicking on links in unsolicited communications
- Rely on verified news outlets and official government websites for election information
- Report suspected phishing or scams through the ScamShield app
- Download apps only from official sources
- Look for visual anomalies and unnatural audio when identifying potential deepfakes.
- Avoid sharing unverified information.
The article notes that Singapore’s general election will be held on May 3, 2025, and this is the first time a new law banning fake online ads will be in place for a general election.
Understanding Election-Related Cyber Threats and Prevention
Let me explain the cyber threats mentioned in the article in greater depth, along with comprehensive prevention strategies.
Detailed Analysis of Cyber Threats
1. Impersonation and Fake Websites
Threat: Fraudsters create counterfeit social media accounts and websites that mimic legitimate political parties or candidates. These fake platforms can:
- Solicit fraudulent donations
- Spread misinformation designed to manipulate voter behaviour
- Harvest personal information and credentials
- Damage a candidate’s reputation through false statements
How it works: Attackers create highly convincing replicas of official websites with nearly identical URLS (e.g., “singapore-elections.com” instead of “elections.gov.sg”) and visual elements. They may also create social media accounts that appear official but contain subtle differences in usernames.
2. AI-Enhanced Phishing
Threat: Artificial intelligence is revolutionising phishing attacks by enabling:
- Highly personalised messages based on your digital footprint
- Natural-sounding voice clones that can impersonate candidates or officials
- Targeted messaging aligned with your political views or interests
How it works: AI analyses your online presence (social media posts, comments, likes) to craft messages that resonate with your specific interests or concerns. For example, if you’ve shown interest in environmental policies, you might receive a fraudulent message about a candidate’s “new green initiative” requiring “urgent donations.”
3. Deepfakes
Threat: Sophisticated AI-generated videos or audio recordings that show candidates saying or doing things they never actually did.
How it works: Using machine learning algorithms, fraudsters can superimpose a candidate’s face onto another person’s body or manipulate existing footage to change what was said. These can spread rapidly on social media and damage a candidate’s reputation before they can be debunked.
4. Malware Distribution
Threat: Malicious software disguised as election-related apps or content that:
- Steals personal data
- Monitors device activity
- Encrypts files for ransom
- Gives attackers remote access to your device
How it works: Attackers create fake campaign apps, voter information tools, or polling location finders that contain hidden malware. These might be distributed through app stores, email attachments, or download links in messages.
5. Data Manipulation
Threat: Though not explicitly mentioned in the article, another concern is the manipulation of voter data or election-related information.
How it works: Attackers might target election databases or official information channels to alter information about polling stations, voting procedures, or candidate details to create confusion or suppress voting.
Comprehensive Prevention Strategies
Digital Literacy and Awareness
- Verify sources: Check official government websites (ending in .gov.sg) for election information.
- Cross-reference news: Confirm information across multiple reliable sources
- Check URLS carefully: Look for subtle misspellings or domain differences
- Question emotional appeals: Be sceptical of messages designed to provoke strong reactions
Technical Protection
- Use official apps: Download election-related applications only from official government sources or verified app stores.
- Enable multi-factor authentication: Protect your accounts with additional verification methods.
- Install security software: Use a reputable antivirus and anti-malware program.
- Keep software updated: Apply security patches promptly to fix vulnerabilities.
- Use a password manager: Create strong, unique passwords for all accounts.
Content Verification
- Examine media critically: Look for visual anomalies in videos (blurring, strange lighting, unnatural movements)
- Check audio-visual sync: In videos, watch for mismatches between lip movements and speech.
- Verify timestamps: Check when content was actually created versus when it claims to be from
- Reverse image search: Use tools like Google Images to verify photographs.
Safe Communication Practices
- Avoid clicking links: Type URLS directly into your browser rather than clicking links in messages.
- Be cautious with attachments: Don’t open files from unknown sources
- Verify requests: Contact organisations directly through official channels if you receive unusual requests
- Use secure messaging: Consider end-to-end encrypted messaging apps for sensitive communications
Reporting and Response
- Report suspicious content: Use the ScamShield app to report potential scams or phishing attempts.
- Notify authorities: Report election-related misinformation to the Elections Department.
- Alert platforms: Report fake accounts or misleading content to social media companies
- Inform others: Share verified information about identified threats with friends and family.
Election-Specific Precautions
- Check candidate information: Verify candidate statements through official channels.
- Donation vigilance: Only donate through official campaign websites after verifying their authenticity
- Polling information: Confirm voting locations and procedures through official government sources
- Scrutinize polls: Be sceptical of unofficial polls or survey results, especially those shared via social media.
By implementing these strategies, Singaporeans can significantly reduce their vulnerability to cyber threats during election season while still fully participating in the democratic process.

Anti-Scam Resources in Singapore
Singapore has developed a robust ecosystem of anti-scam resources to combat the rising threat of scams. Here’s a comprehensive overview of the help available:
Government Agencies and Helplines

ScamShield
- What it is: A mobile app developed by the National Crime Prevention Council (NCPC) and Government Technology Agency (GovTech)
- Features:
- Blocks suspected scam calls and messages
- Allows reporting of scam attempts
- Available for both ios and Android
- How it works: The app filters calls from phone numbers used in previously reported scam cases and filters out suspicious SMS messages.

Anti-Scam Centre (ASC)
- What it is: A specialised unit set up by the Singapore Police Force
- Services:
- Disrupts scammers’ operations
- Works with banks to freeze suspicious accounts
- Helps recover stolen funds when possible
- Hotline: 1800-255-0000
NCPC Scam Alert Website (scamalert.sg)
- Features:
- Latest information on scam trends
- Educational resources
- Reporting mechanism for scams
Report Scams Portal
- URL: www.scamalert.sg/report
- Purpose: Centralised platform to report various types of scams
Banking Protection Measures
Anti-Scam Initiatives by Banks
- Pre-transaction screening
- Cooling-off periods for large or unusual transactions
- SMS alerts for transactions
- Transaction limits on mobile banking
Bank-Specific Hotlines
Most major banks have dedicated anti-scam hotlines:
- DBS: 1800-339-6963
- OCBC: 1800-363-3333
- UOB: 1800-222-2121
- Standard Chartered: 1800-747-7000
Community Support
Scam Support Centre
- What it is: Support centre for scam victims
- Services:
- Emotional support
- Practical advice
- Guidance on recovery steps
NCPC Jaga (Watch) Your Data
- A community initiative encouraging vigilance regarding personal data
Educational Resources
Spot the Signs Campaign
- Public education campaign teaching citizens to identify common scam patterns.
Inter-Ministry Committee on Scams
- Coordinates anti-scam efforts across government agencies
- Produced educational materials and campaigns

What to Do If You’ve Been Scammed
- Report immediately to the Police at 999 for urgent cases or 1800-255-0000
- Contact your bank to freeze accounts or stop transactions
- Preserve evidence like messages, emails, and transaction details
- Report online scams at www.scamalert.sg/report
- Change passwords for compromised accounts
- Monitor accounts for suspicious activity
- Seek support from the Scam Support Centre if needed
Prevention Best Practices
- Use ScamShield app
- Verify information through official channels
- Never share OTPS, passwords, or personal details
- Be sceptical of unexpected messages about prizes or urgent requests
- Check bank statements regularly
- Keep software updated on all devices
- Use strong, unique passwords and enable two-factor authentication
Singapore’s multifaceted approach effectively combats scams by combining technology, education, enforcement, and community support. The integration of these resources provides Singaporeans with comprehensive protection against increasingly sophisticated scam attempts.
Maxthon
Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
